SSO/SAML & SCIM
This is a Pro Licence feature
SSO/SAML
With a Fusion Signage Pro Licence, you have access to Single Sign-On/SAML/Federated User Management to control your users’ access to the Fusion Signage portal.
Here’s how to set up SAML authentication between Fusion Signage and Azure Active Directory.
Prerequisites
- Only Pro Licences on your account
- An enterprise app that has been created in Active Directory and is setup to use SAML for SSO.
- Users are present in both systems with the same identifier (email address)
Enabling This Function
At this stage this function needs to be enabled internally, if this is a feature you would like to be using please contact our friendly support team at support@fusionsignage.com.au and we can turn this feature on for you.
Fusion Signage SP Metadata
- Log into your Fusion Signage account at https://app.fusionsignage.com.au/
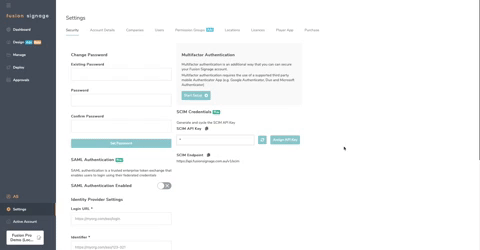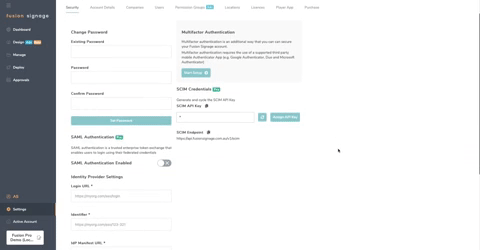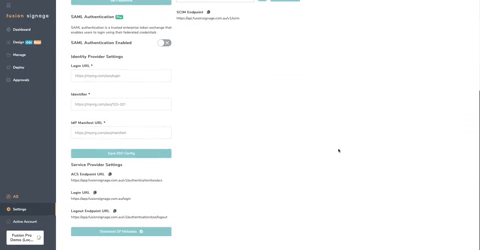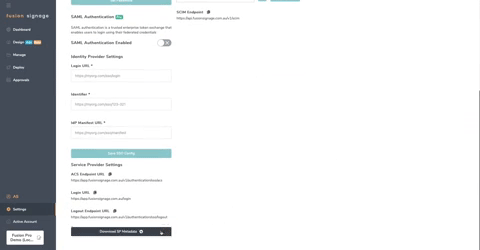
- Navigate to Settings > Security
- Here you will find all of the relevant information you will need to connect Fusion Signage to your Azure Active Directory
- Scroll to the bottom of the page and Click the button labelled Download SP Metadata and save that file to your computer.
Enterprise App
- Navigate to Single sign-on
- Click Upload metadata file and upload the file you just downloaded
- Copy Login URL from Fusion Signage CMS and paste into Sign on URL: https://app.fusionsignage.com.au/login
- Copy Redirect URL from Fusion Signage CMS and paste into Relay State: https://app.fusionsignage.com.au/
- Click Save
Microsoft Entra ID (Azure AD)’s SAML‑based Single Sign‑On certificates are self‑signed and have a fixed lifetime: three years from the date of creation
You cannot extend an existing certificate’s expiration. Instead, you must:
- Generate a new SAML certificate (valid up to 3 years ahead)
- Go to Enterprise apps -> Fusion Signage -> single sign on -> SAML certificates -> click edit -> click new certificate
- Set the new certificate as Active
- Mark the old one Inactive
Fusion Signage CMS
- Navigate back to your Fusion Signage portal at https://app.fusionsignage.com.au
- Copy Login URL from Enterprise App and paste into Login URL within the Fusion Signage portal under Settings -> Security.
- Copy Azure AD Identifier from Enterprise App and paste into Identifier
- Copy App Federation Metadata Url from Enterprise App and paste into IdP Manifest URL
- Click Save SSO Config
Login
- Navigate to the Fusion Signage login page at https://app.fusionsignage.com.au/
- Click Log in with SSO from the login page
- Enter your federated email address and click Login
SCIM (System for Cross-domain Identity Management)
This feature allows users to be automatically synchronised between the identity provider(iDP) and the service provider(SP) which means that users can be managed entirely on the iDP side and then they flow to the application where users are created as assigned groups automatically.
Requirements:
Active Directory Enterprise Application
- Users assigned to this application
- An API key for authenticating the service level requests
- a URL for the service to communicate with (SCIM endpoint)
Setup the enterprise application
- Within Active Directory, navigate to Provisioning
- Select Edit Provisioning
- Enter the admin credentials here
- Tenant URL - this will be the SCIM endpoint of Fusion Signage
- Secret Token - the API key that was generated as part of this access
- Test the connection to confirm that this is all correct and click Save
- Expand Mappings and select Provision Azure Active Directory Users
- The mappings are required to map to Fusion Signage
- Ensure that this set of attributes are Enabled and click Save
You will need the SCIM feature toggled on in order to use this feature. Please email support@fusionsignage.com.au to request this feature be enabled for your company.
- Once the SCIM Provisioning feature has been turned on, refresh your browser and navigate to the security tab, you should be able to see the SCIM Credentials.
- click the refresh symbol to generate an API Key and click Assign API Key to save it.
- copy this key (by clicking the copy to clipboard icon next to the SCIM API Key heading)
- Enter this into the credentials part of the enterprise application and click Test Connection to ensure that the credentials are working
Add Users
- Within the enterprise application navigate to Users and Groups
- Add users that need to be synchronised
Start the Sync
- From the Provisioning menu option, click the Start Provisioning button to start the process
Group Synchronisation
SCIM also facilitates the ability to sync groups to the platform, these are just logical groupings of users. Note: The concept of user groups may need to be implemented into your platform
Each user object that gets synchronised follows a similar flow as the users sync.
- Group is synced without users in a payload containing it's name, externalId and no users
- This gets parsed in the API and created accordingly
- The next step is for each user to be syncronised as an add operation for the group object
- The user is queried for its existence on the SP side and if preset it is processed accordingly
- If the user doesn't exist in the SP the same flow for user creation occurs before being assigned to the group
SCIM with respect to Azure Provisioning only uses 3 rest verbs to achieve the outcome.
- GET to fetch the resource by the externalId
- POST to create the resource on the SP
- PATCH to update the resource